Introduction
I use the function on my yubikey every day to log on to servers as if by magic. It is not necessary to enter a password every time. After a while you get used to this convenience and find it annoying to enter the password every time to unlock the PC. As I have to take the Yubikey with me every time I leave the workplace anyway, I asked myself whether it is also possible to unlock the PC using the Yubikey.
After a bit of research on the Internet, I found the right snippets here and there. The result looks like this
whats needed?
First of all, of course, you need a Yubikey. Everything else is free and may vary slightly depending on the setup.
The following items are also required:
- udev (available with every Linux)
- the following packages
- libpam-yubico
- yubikey-personalization
- yubikey-manager
- pamtester
Setup
Challenge Response Setup
After you have installed the required stuff you should set up a CR (challenge response) in slot 2 of your Yubikey
To enable challenge-response on your Yubikey in slot 2, type the following command:
ykman otp chalresp -g 2This configures slot 2 for challenge-response, and leaves slot 1 alone.
Next we need to create a place to store your challenge response files, secure those files, and finally create the stored challenge files:
sudo mkdir /etc/yubico
sudo chown root /etc/yubico
sudo chmod 700 /etc/yubico
ykpamcfg -2 -vYou should receive a message similar to:
Stored initial challenge and expected response in '$HOME/.yubico/challenge-123456'.
You should receive a unique challenge-serial in your output.
Now, to finish up:
sudo mv ~/.yubico/challenge-123456 /etc/yubico/yubikey-serial
sudo chown root.root /etc/yubico/yubikey-serial
sudo chmod 600 /etc/yubico/yubikey-serialPay close attention when copying/pasting the commands above. The challenge-123456 and yubikey-serial needs to match the both the output from the ykpamcfg command and the final file needs to match the name of your user name and serial.
PAM Setup to use CR for unlock/login
Since we realize the whole thing via the pam, the Yubikey can not only be used to unlock the current session but also when logging in to a shell (local tty)
For this to work, we have to equip our pam.d with new configuration parameters accordingly.
I have added the following line to the system-local-login in /etc/pam.d
auth sufficient pam_yubico.so mode=challenge-response chalresp_path=/etc/yubicothe complete file looks like this:
#%PAM-1.0
auth sufficient pam_yubico.so mode=challenge-response chalresp_path=/etc/yubico
auth include system-login
account include system-login
password include system-login
session include system-loginNow we can already test the login. Switch to a local tty and try to log in with your user. The console should not request a password if the yubikey is inserted.
yes, that's really fun too, but it gets even better
udev rules
Every time a device is inserted or removed, udev is triggered. udev itself can execute scripts based on rules that we can define. It is precisely this functionality that we make use of. So we create a rule for our yubikey. If the yubikey is plugged into a USB port, a script should be executed by us. Likewise when the yubikey is removed
We need some information so that the udev rule is used by the correct device. We get this by entering lsusb
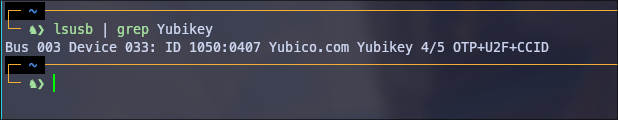
everything behind ID is needed by us immediately
here are the udev rule for my /etc/udev/rules.d/99-yubikey.rules
SUBSYSTEM=="usb", ATTRS{idVendor}=="1050", ATTRS{idProduct}=="0407", GROUP="wheel", TAG+="uaccess"
ACTION=="remove", ENV{DEVTYPE}=="usb_device", ENV{PRODUCT}=="1050/407*", RUN+="/usr/local/bin/ykcheck.sh lock"
ACTION=="add", ENV{DEVTYPE}=="usb_device", ENV{ID_BUS}=="usb", ENV{PRODUCT}=="1050/407*", RUN+="/usr/local/bin/ykcheck.sh unlock"after saving this file a reload of udev is needed.
sudo udevadm control --reload-rules && sudo udevadm triggerThe ykcheck.sh script
Now that our udev rule is set up, we need to store the script that is started by the udev rule in the appropriate place.
The ykcheck.sh script should be stored in /usr/local/bin/ and be executable (chmod o+x ykcheck.sh)
#!/bin/bash
exec 1> >(logger -s -t "$(basename "$0")") 2>&1
echo "YKCHECK RUN"
sessionid=$(loginctl list-sessions --no-legend | awk '$4 != "-" { print $1 }')
echo "YKCHECK SESSIONID $sessionid"
if [ "$1" == "lock" ]; then
# pkill -USR1 swayidle
loginctl lock-session $sessionid
else
# unlock
if echo "" | pamtester login bigfreak authenticate; then
# PAM login successful
# kill locker
# kill -SIGUSR1 $(pgrep hyprlock)
loginctl unlock-session $sessionid
fi
fi
exit 0Now your desktop environment should be unlocked when you plug in the yubikey. The GUI should also lock when you remove the yubikey.
I use sway and swayidle handles the dbus event that comes from loginctl. Maybe your Desktopenvironment does not handle this. i have some comments in the ykcheck.sh. for helping to find out how your session manager gets info about the lock/unlock event.
